OSA Landscape
In order to determine that OSA has the correct topic coverage we need to define the landscape for security architecture. That way we can identify topics that have poor coverage, determine priorities for new patterns, and help the community co-ordinate their activities.
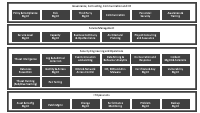
OSA Process Landscape
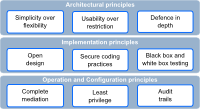
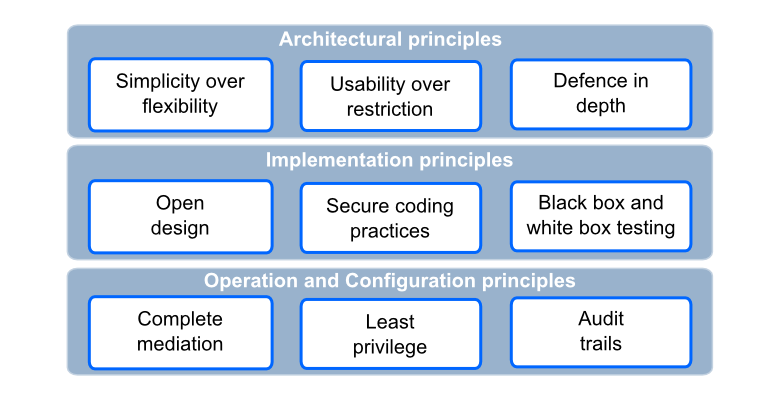
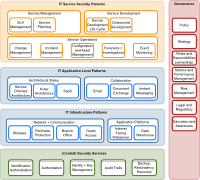
The OSA process landscape arranges typical IT (security) processes into areas or capabilities. We differentiate between a pattern landscape which defines architectural patterns of interest, and a process landscape where the purpose is to define expected activities by a Cyber Security function in an organisation.

OSA Actors
In OSA patterns we refer to a number of generic roles, we call them actors. To ensure the consistency between the patterns we collect the description of these actors centrally.

OSA Lifecycle
The OSA community has not yet decided on the primary reference model in terms of SDLC (Solution/System/Software Development Life Cycle). Help us decide!

How to use OSA
OSA offers readily re-usable material on several abstraction layers. On the top level, OSA provides an overall landscape, actors (soon coming) as well as a terminology and taxonomy. On the next level OSA provides security patterns and finally OSA provides a threat modeling and a (NIST based) controls catalog.
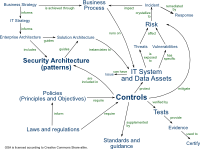
OSA Taxonomy
The OSA Taxonomy depicts the entities and relationships that are relevant for OSA. The taxonomy helps to understand how OSA is related to other security concepts, and allows us to consider how we will develop OSA in the future.

Links to related
In this section anyone with Author status can post articles about their favorite links to IT security architecture related material. We follow the same quality policy as Wikipedia and take the liberty to delete articles that might not be up to common sense quality standards.