|
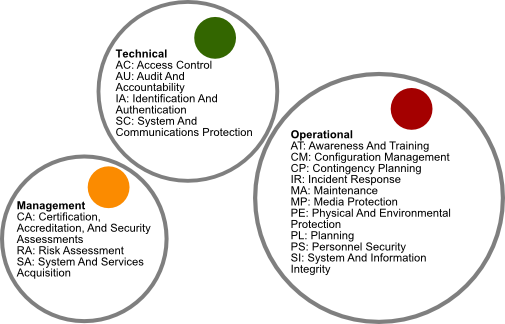
13-05 All Controls
|
Hits: 28206
|
|
13-05 Control mapping (NIST 800-53 vs ISO 17799 / PCI-DSS v2 / COBIT 4.1
|
Hits: 70224
|
|
13-05 Controls catalog SQL export
|
Hits: 9908
|
|
AC-01 Access Control Policies and Procedures
|
Hits: 44915
|
|
AC-02 Account Management
|
Hits: 28845
|
|
AC-03 Access Enforcement
|
Hits: 32217
|
|
AC-04 Information Flow Enforcement
|
Hits: 33481
|
|
AC-05 Separation Of Duties
|
Hits: 18327
|
|
AC-06 Least Privilege
|
Hits: 18217
|
|
AC-07 Unsuccessful Login Attempts
|
Hits: 17170
|
|
AC-08 System Use Notification
|
Hits: 14814
|
|
AC-09 Previous Logon Notification
|
Hits: 12856
|
|
AC-10 Concurrent Session Control
|
Hits: 14364
|
|
AC-11 Session Lock
|
Hits: 16640
|
|
AC-12 Session Termination
|
Hits: 15368
|
|
AC-13 Supervision And Review -- Access Control
|
Hits: 11250
|
|
AC-14 Permitted Actions Without Identification Or Authentication
|
Hits: 10050
|
|
AC-15 Automated Marking
|
Hits: 8628
|
|
AC-16 Automated Labeling
|
Hits: 8020
|
|
AC-17 Remote Access
|
Hits: 16718
|
|
AC-18 Wireless Access Restrictions
|
Hits: 15506
|
|
AC-19 Access Control For Portable And Mobile Devices
|
Hits: 15196
|
|
AC-20 Use Of External Information Systems
|
Hits: 15003
|
|
AT-01 Security Awareness And Training Policy And Procedures
|
Hits: 17305
|
|
AT-02 Security Awareness
|
Hits: 15521
|
|
AT-03 Security Training
|
Hits: 15000
|
|
AT-04 Security Training Records
|
Hits: 10329
|
|
AT-05 Contacts With Security Groups And Associations
|
Hits: 8518
|
|
AU-01 Audit And Accountability Policy And Procedures
|
Hits: 18647
|
|
AU-02 Auditable Events
|
Hits: 24356
|
|
AU-03 Content Of Audit Records
|
Hits: 15009
|
|
AU-04 Audit Storage Capacity
|
Hits: 12226
|
|
AU-05 Response To Audit Processing Failures
|
Hits: 15226
|
|
AU-06 Audit Monitoring, Analysis, And Reporting
|
Hits: 31374
|
|
AU-07 Audit Reduction And Report Generation
|
Hits: 15280
|
|
AU-08 Time Stamps
|
Hits: 11980
|
|
AU-09 Protection Of Audit Information
|
Hits: 15258
|
|
AU-10 Non-Repudiation
|
Hits: 16088
|
|
AU-11 Audit Record Retention
|
Hits: 13763
|
|
CA-01 Certification, Accreditation, And Security Assessment Policies And Procedures
|
Hits: 15298
|
|
CA-02 Security Assessments
|
Hits: 19002
|
|
CA-03 Information System Connections
|
Hits: 11228
|
|
CA-04 Security Certification
|
Hits: 13989
|
|
CA-05 Plan Of Action And Milestones
|
Hits: 10109
|
|
CA-06 Security Accreditation
|
Hits: 11781
|
|
CA-07 Continuous Monitoring
|
Hits: 17385
|
|
CM-01 Configuration Management Policy And Procedures
|
Hits: 16563
|
|
CM-02 Baseline Configuration
|
Hits: 19026
|
|
CM-03 Configuration Change Control
|
Hits: 17307
|
|
CM-04 Monitoring Configuration Changes
|
Hits: 11708
|
|
CM-05 Access Restrictions For Change
|
Hits: 14792
|
|
CM-06 Configuration Settings
|
Hits: 14265
|
|
CM-07 Least Functionality
|
Hits: 21505
|
|
CM-08 Information System Component Inventory
|
Hits: 15360
|
|
CP-01 Contingency Planning Policy And Procedures
|
Hits: 11893
|
|
CP-02 Contingency Plan
|
Hits: 12048
|
|
CP-03 Contingency Training
|
Hits: 9983
|
|
CP-04 Contingency Plan Testing And Exercises
|
Hits: 17357
|
|
CP-05 Contingency Plan Update
|
Hits: 9136
|
|
CP-06 Alternate Storage Site
|
Hits: 10384
|
|
CP-07 Alternate Processing Site
|
Hits: 12679
|
|
CP-08 Telecommunications Services
|
Hits: 7596
|
|
CP-09 Information System Backup
|
Hits: 15284
|
|
CP-10 Information System Recovery And Reconstitution
|
Hits: 14375
|
|
IA-01 Identification And Authentication Policy And Procedures
|
Hits: 18046
|
|
IA-02 User Identification And Authentication
|
Hits: 24479
|
|
IA-03 Device Identification And Authentication
|
Hits: 21023
|
|
IA-04 Identifier Management
|
Hits: 14681
|
|
IA-05 Authenticator Management
|
Hits: 17630
|
|
IA-06 Authenticator Feedback
|
Hits: 12170
|
|
IA-07 Cryptographic Module Authentication
|
Hits: 17931
|
|
IR-01 Incident Response Policy And Procedures
|
Hits: 13317
|
|
IR-02 Incident Response Training
|
Hits: 11473
|
|
IR-03 Incident Response Testing And Exercises
|
Hits: 13815
|
|
IR-04 Incident Handling
|
Hits: 21185
|
|
IR-05 Incident Monitoring
|
Hits: 11601
|
|
IR-06 Incident Reporting
|
Hits: 11535
|
|
IR-07 Incident Response Assistance
|
Hits: 11849
|
|
MA-01 System Maintenance Policy And Procedures
|
Hits: 12000
|
|
MA-02 Controlled Maintenance
|
Hits: 12667
|
|
MA-03 Maintenance Tools
|
Hits: 11012
|
|
MA-04 Remote Maintenance
|
Hits: 12608
|
|
MA-05 Maintenance Personnel
|
Hits: 9025
|
|
MA-06 Timely Maintenance
|
Hits: 10094
|
|
MP-01 Media Protection Policy And Procedures
|
Hits: 11615
|
|
MP-02 Media Access
|
Hits: 11530
|
|
MP-03 Media Labeling
|
Hits: 8310
|
|
MP-04 Media Storage
|
Hits: 8736
|
|
MP-05 Media Transport
|
Hits: 8911
|
|
MP-06 Media Sanitization And Disposal
|
Hits: 9794
|
|
PE-01 Physical And Environmental Protection Policy And Procedures
|
Hits: 11186
|
|
PE-02 Physical Access Authorizations
|
Hits: 9756
|
|
PE-03 Physical Access Control
|
Hits: 12590
|
|
PE-04 Access Control For Transmission Medium
|
Hits: 9521
|
|
PE-05 Access Control For Display Medium
|
Hits: 8721
|
|
PE-06 Monitoring Physical Access
|
Hits: 11329
|
|
PE-07 Visitor Control
|
Hits: 7740
|
|
PE-08 Access Records
|
Hits: 6682
|
|
PE-09 Power Equipment And Power Cabling
|
Hits: 9159
|
|
PE-10 Emergency Shutoff
|
Hits: 8660
|
|
PE-11 Emergency Power
|
Hits: 8278
|
|
PE-12 Emergency Lighting
|
Hits: 8414
|
|
PE-13 Fire Protection
|
Hits: 8783
|
|
PE-14 Temperature And Humidity Controls
|
Hits: 8326
|
|
PE-15 Water Damage Protection
|
Hits: 8415
|
|
PE-16 Delivery And Removal
|
Hits: 8731
|
|
PE-17 Alternate Work Site
|
Hits: 6875
|
|
PE-18 Location Of Information System Components
|
Hits: 6875
|
|
PE-19 Information Leakage
|
Hits: 8461
|
|
PL-01 Security Planning Policy And Procedures
|
Hits: 15361
|
|
PL-02 System Security Plan
|
Hits: 10492
|
|
PL-03 System Security Plan Update
|
Hits: 6171
|
|
PL-04 Rules Of Behavior
|
Hits: 11774
|
|
PL-05 Privacy Impact Assessment
|
Hits: 8276
|
|
PL-06 Security-Related Activity Planning
|
Hits: 6462
|
|
PS-01 Personnel Security Policy And Procedures
|
Hits: 12634
|
|
PS-02 Position Categorization
|
Hits: 7180
|
|
PS-03 Personnel Screening
|
Hits: 7882
|
|
PS-04 Personnel Termination
|
Hits: 6574
|
|
PS-05 Personnel Transfer
|
Hits: 6183
|
|
PS-06 Access Agreements
|
Hits: 11174
|
|
PS-07 Third-Party Personnel Security
|
Hits: 10900
|
|
PS-08 Personnel Sanctions
|
Hits: 7927
|
|
RA-01 Risk Assessment Policy And Procedures
|
Hits: 11584
|
|
RA-02 Security Categorization
|
Hits: 14028
|
|
RA-03 Risk Assessment
|
Hits: 15938
|
|
RA-04 Risk Assessment Update
|
Hits: 10745
|
|
RA-05 Vulnerability Scanning
|
Hits: 18332
|
|
SA-01 System And Services Acquisition Policy And Procedures
|
Hits: 15908
|
|
SA-02 Allocation Of Resources
|
Hits: 11949
|
|
SA-03 Life Cycle Support
|
Hits: 14036
|
|
SA-04 Acquisitions
|
Hits: 13132
|
|
SA-05 Information System Documentation
|
Hits: 21999
|
|
SA-06 Software Usage Restrictions
|
Hits: 10639
|
|
SA-07 User Installed Software
|
Hits: 10362
|
|
SA-08 Security Engineering Principles
|
Hits: 17567
|
|
SA-09 External Information System Services
|
Hits: 12883
|
|
SA-10 Developer Configuration Management
|
Hits: 11542
|
|
SA-11 Developer Security Testing
|
Hits: 10144
|
|
SC-01 System And Communications Protection Policy And Procedures
|
Hits: 14000
|
|
SC-02 Application Partitioning
|
Hits: 13065
|
|
SC-03 Security Function Isolation
|
Hits: 15670
|
|
SC-04 Information Remnance
|
Hits: 16819
|
|
SC-05 Denial Of Service Protection
|
Hits: 15526
|
|
SC-06 Resource Priority
|
Hits: 10672
|
|
SC-07 Boundary Protection
|
Hits: 26371
|
|
SC-08 Transmission Integrity
|
Hits: 18031
|
|
SC-09 Transmission Confidentiality
|
Hits: 16854
|
|
SC-10 Network Disconnect
|
Hits: 11193
|
|
SC-11 Trusted Path
|
Hits: 13664
|
|
SC-12 Cryptographic Key Establishment And Management
|
Hits: 14809
|
|
SC-13 Use Of Cryptography
|
Hits: 15749
|
|
SC-14 Public Access Protections
|
Hits: 9451
|
|
SC-15 Collaborative Computing
|
Hits: 12062
|
|
SC-16 Transmission Of Security Parameters
|
Hits: 7172
|
|
SC-17 Public Key Infrastructure Certificates
|
Hits: 8049
|
|
SC-18 Mobile Code
|
Hits: 16454
|
|
SC-19 Voice Over Internet Protocol
|
Hits: 6821
|
|
SC-20 Secure Name / Address Resolution Service (Authoritative Source)
|
Hits: 15989
|
|
SC-21 Secure Name / Address Resolution Service (Recursive Or Caching Resolver)
|
Hits: 9172
|
|
SC-22 Architecture And Provisioning For Name / Address Resolution Service
|
Hits: 8806
|
|
SC-23 Session Authenticity
|
Hits: 17135
|
|
SI-01 System And Information Integrity Policy And Procedures
|
Hits: 12664
|
|
SI-02 Flaw Remediation
|
Hits: 22679
|
|
SI-03 Malicious Code Protection
|
Hits: 21030
|
|
SI-04 Information System Monitoring Tools And Techniques
|
Hits: 23060
|
|
SI-05 Security Alerts And Advisories
|
Hits: 12439
|
|
SI-06 Security Functionality Verification
|
Hits: 17628
|
|
SI-07 Software And Information Integrity
|
Hits: 16693
|
|
SI-08 Spam Protection
|
Hits: 8051
|
|
SI-09 Information Input Restrictions
|
Hits: 8282
|
|
SI-10 Information Accuracy, Completeness, Validity, And Authenticity
|
Hits: 17012
|
|
SI-11 Error Handling
|
Hits: 12436
|
|
SI-12 Information Output Handling And Retention
|
Hits: 9887
|